SYSTEM SAFETY
Safety is, of course, key in the design, manufacture, testing & commissioning and delivery phases of any product or system. Designers need to ensure that the overall goal of a system is achieved, including the engineering safety, to ensure that the service performance objectives are delivered. System safety is determined by the residual risk of the boundary hazards exported to its environment. System safety takes account of the functional safety requirements.
We work closely with clients from the outset of a project to analyze the design development during the project life-cycle stages in accordance with the standards and the contract specifications and clearly define Safety requirements so that these can be implemented and integrated into the various project phases. We practice industry-specific safety techniques to provide assurance that the required levels of safety has been achieved in the design and function of the systems. Our team undertakes various safety analyses to identify and record safety issues and ensure that these are mitigated during the design development. Further, we liaise with the client’s Safety Authorities & ISA (Independent Safety Assessor) to trace safety compliance for systems and secure system acceptance on each project.
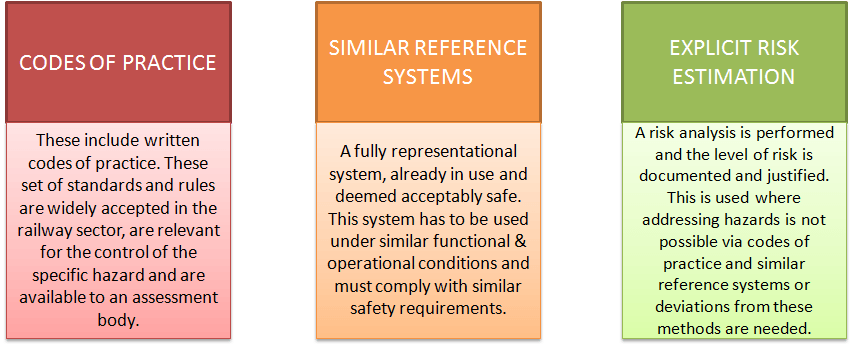
To describe how the safety levels, achievement of safety targets and compliance with other safety requirements are fulfilled, we use these Common Safety Methods (CSM)-
We choose appropriate safety assessment techniques to be implemented on each project, such as:
- Hazard Identification (HAZID)
- Hazard and Operability (HAZOP)
- Qualitative and Quantitative Risk Analysis (QRA)
- Interface Hazard Analysis (IHA)
- Operation and Support Hazard Analysis (OSHA)
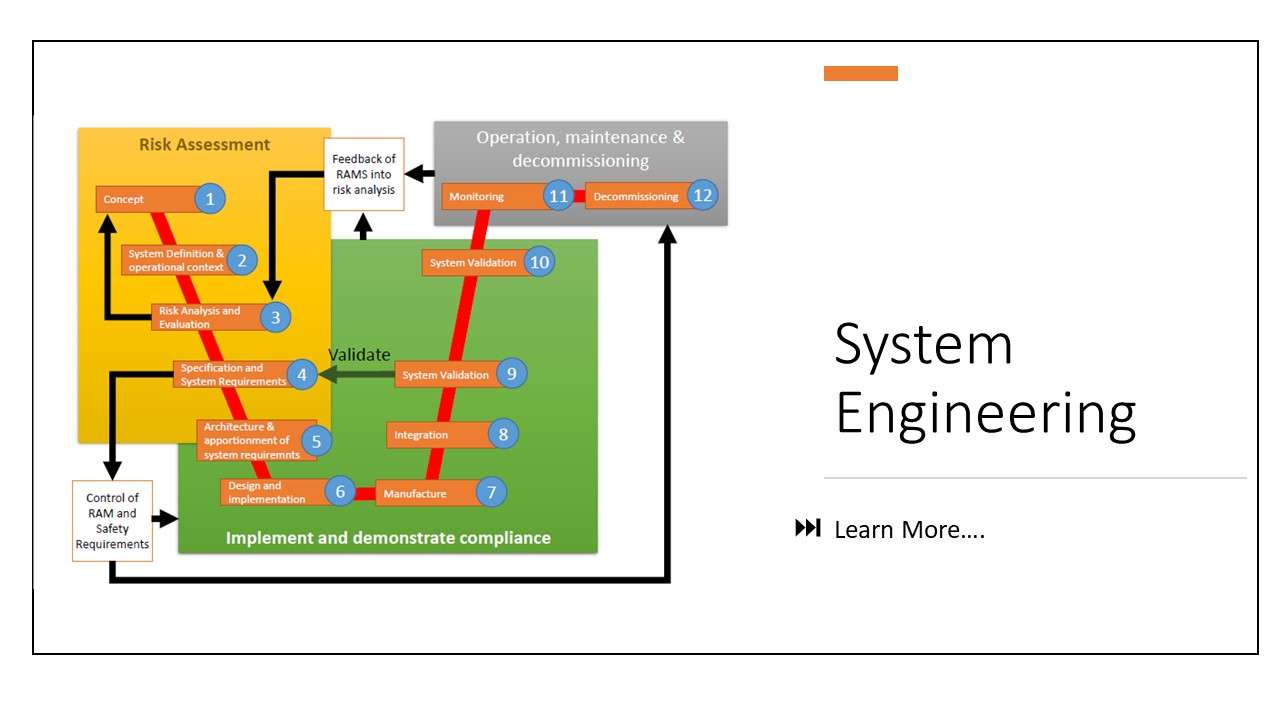
System safety process includes conducting a risk assessment process followed by hazard control process.
Risk assessment is performed at the railway system level. It relies on system definition and includes Risk analysis and Risk evaluation. The risk assessment includes the preliminary system definition which also includes the PHA. After this process, a full system definition is required which is in more detail compared to the previous step. This is followed by the Hazard identification and classification. The next step is risk acceptance in accordance with appropriate selection of the Risk acceptance principles recognized in the Common Safety Methods. We demonstrate through safety cases that after applying these principles, the risk is within acceptable limits. As part of safety demonstration, we elicit safety requirements from hazard mitigations and demonstrate compliance with the safety requirements.
When a hazard is identified, it is recorded in a document- The Hazard Log. This log is used to track hazards from their point of first identification, determining and recording which mitigations are necessary and finally ensuring that the level of risk is acceptable. This is a live document which is used as a database and can be referred for evidence of safety demonstration at any point during the project life-cycle. We identify all credible hazards by using these techniques- HAZOP, HAZID checklist, functional failure analysis, structure what-if techniques. FMEA etc. These hazards which are identified using these activities, are recorded in the hazard log and are mitigated during the design development phase. Further, we work together with the design and test engineers to collect evidences for these mitigations to verify and validate that the risk is acceptable. The hazard log provides a central control and trace-ability of hazard and risk management activities throughout the project cycle.
The deliverables produced during the hazard control process are listed below.
We produce tailored deliverables for all projects to satisfy project safety requirements plus comply with industry and national standards. Some key deliverables are-
Preliminary Hazard Analysis (PHA)
This is the initial effort in hazard analysis during the system design phase or the programming or requirements development phase for facilities acquisition. The purpose of the PHA is to fully recognize the hazardous states with all accompanying safety implications.
Interface Hazard Analysis (IHA)
The purpose is to identify and mitigate the key hazards arising from system interfaces. This document is a key element of the Hazard Log.
System and Sub-System Hazard analysis (SSHA)
This analysis examines each subsystem or component and identifies hazards associated with it.
Operational and Support Hazard Analysis (OSHA)
This is performed primarily to identify and evaluate the hazards associated with the environment, personnel, procedures, operation, support and equipment involved throughout the total life cycle of a system/element.
Hazard Analysis and Hazard Log
A Hazard Log is a central document for showing the professional and appropriate management of risk. The purpose of this document is to record all identified hazards and list the proposed mitigations and collect evidences to verify and validate that the residual risk is lowered.
Engineering Safety Validation Plan & Report
This plan describes the structured process to be implemented by for the validation of the safety requirements. The report documents how closely the plan was followed and its results.
System Safety Plan
The purpose of this document is to define the framework Safety and activities to be undertaken for the system in consideration to meet the Safety requirements.
Safety Cases
The purpose of this document is to establish that the system complies to all the safety requirements and that it is ready and safe for operation. This documents that all necessary test procedures and acceptance criteria are in place and that the system has completed and passed all safety tests. Generally, these two are produced for a project-
-Design Safety Case (includes verification evidences of mitigation of hazards)
-Application Safety Case (includes validation evidences of mitigation of hazards)